For embedded systems and IoT devices, data management security is critical because of the roles that these mission-critical machines play in our lives. Insecure data management practices and systems create a tremendous number of vulnerabilities and risks. Data and data management software are essential for the accuracy and dependability of these intelligent devices. Manufactures of IoT devices and embedded systems must recognize the data management security risks and available options when they design, develop, and deploy their systems. Here are few important security suggestions for edge devices:
Database inconsistency: Developers of embedded systems and devices need to plan consistent database development practices. This includes verifying that the same database version is used for both development and deployment, including updates and upgrades. Development managers also need to cultivate a clear communication between the team members for applicable standards, policies, and maintenance changes.
Vulnerability assessment: An interesting consideration would be to document the attack surface of the application and keep it continuously updated. Such a document identifies the attacks against which the device application needs to have defense. It is important to have designers, developers, and testers all understand and contribute to this document.
SQL injection: Many common exploits use SQL injection to circumvent database security by tricking an application into executing queries not intended by its developers. Attacks range from classic in-band SQL injection to sophisticated boolean and time-based techniques that blindly probe for information. Database products that allow non-standard SQL syntax to expand the attack surface available for injection. While recommended coding practices, such as parameterized queries, can block SQL injection attacks, these vulnerabilities can be difficult to identify in large applications with various communication channels, including web services.
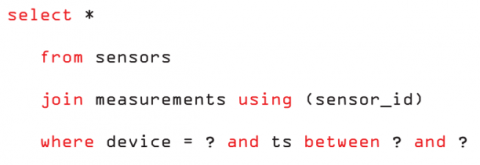
Network protocols: Custom protocols may be susceptible to buffer overruns and other type-safety vulnerabilities that can crash applications and services. In the worst case, arbitrary code execution can provide a channel for other attacks, such as privilege escalation. CPU resources inside the database, database code size, and communication protocols are important gates for monitoring security. But many developers decide to not include security features with their application as they slow down the system or consume too much memory.
By incorporating an extra layer of protection into the database itself, this combination will offer great data protection. Therefore, regular updates of both platform-level and database-level software security practices will offer the best security protection.
ITTIA Security Offering for Edge Devices
While the ITTIA DB Console allows developers and end-users to monitor database activities, DB-SEAL™ isolates databases stored on devices, decides between alternatives to mitigate an attack, and keeps the database contents always available. This proactive monitoring of the data and database by DB-SEAL will allow the device to issue an alert, block access, or shut down when data management metrics fall out of the expected range.
In addition to DB-SEAL, ITTIA DB SQL offers secure file storage, remote access, and replication. Whether a database file is accessed locally, or is shared over a public network, encryption support ensures that data is protected from unauthorized access, eavesdropping, and session hijacking.
To learn more about embedded edge data management and security, read our Embedding Security for IoT Device Data White Paper.
For more information, contact ITTIA.
